We started using Splunk to serve as a SIEM. In addition to correlating security information, we have begun to use it as a developer and customer advocate by analyzing user behaviors and system response times.

We started using Splunk to serve as a SIEM. In addition to correlating security information, we have begun to use it as a developer and customer advocate by analyzing user behaviors and system response times.
Log files which were previously either not reviewed or reviewed incompletely are now being used in operations daily. Security and operational events are discovered and resolved with greater efficiency than we have ever before. The way Splunk allows for data to be correlated together has given our organization a more complete picture of our system security status and how users organically move through our applications. This information has allowed us to focus development efforts which will directly benefit our customers the most.
The ability to manipulate data in Splunk is unparalleled. Splunk’s powerful, flexible query language can morph difficult to understand log formats into usable data.
Correlating data across different systems via one interface will allow you to know your environment or identify incident data in ways you never imagined.
There is a definite learning curve to starting out. However, there is quite a bit of documentation out there to help you get started.
The community (Splunk Answers/Slack Channel/User Groups) can help get you started.
We previously used ArcSight, but found Splunk to be more cloud capable.
Truly evaluate the data you want to ingest and go slow. Pulling in data that can provide no use to your mission only wastes data against your license.
Other options were evaluated, such as ELK, but Splunk was identified to be more feature rich out-of-the-box.
Pick it up and jump into the community! It can help get you started a lot faster.
SIEM posts have grown in number at Infosecnirvana, but the requests to write about more products keep coming in. One of the oft asked about product is Splunk Enterprise. We have posted on HP ArcSight, IBM QRadar and McAfee Nitro SIEM. However, readers have been asking us repeatedly to write on Splunk.
So here it is finally after being in the works for a long time.
Introduction:
In 2003, One of the most interesting products rolled out and vowed to simplify Log management once and for all (and it did!!!) - Splunk. Their motto was simple – Throw logs at me and I will provide a web based console to search through it intuitively. Interestingly they are one of the few companies that have not been acquired, in spite of being a very innovative product. So let’s see what makes Splunk tick.
Architecture:
As always, a product is as good as its architecture. It has to be solid both internally as well as externally (meaning solution deployment, integration, ease of use, compatibility etc.).
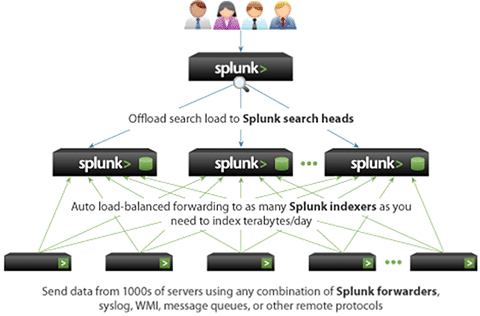
As you can see, there are three distinct components of this architecture and they are as follows:
What’s good about Splunk?
What’s bad?
Conclusion: In our opinion, Splunk is one of the most innovative log management tools out there. But as a SIEM, to use in day to day security management, monitoring, ticketing etc. it has a lot of catching up to do. The ideal scenario will be to use Splunk in the log management layer and use any market leading SIEM in the correlation, workflow and operational management layer. We have seen several successful implementations where Splunk serves as the log management tool and ArcSight or QRadar serves as the Correlation engine. Best of both worlds!!!
I use Splunk for testing purposes. It is used for school research and to learn how to use Splunk.
Splunk is mainly used for collecting logs and dashboards.
Splunk provides a free version so you can test it before purchasing. It's better than IBM, in my opinion, because it's an independent entity. IBM, for example, if you want to use EDR, and other features, you must use the features of other companies, such as ServiceNow and Jira.
I am still exploring the features provided in Splunk. As I have not used it for a long time, I don't have a clear vision of it.
As a student, I'd like to see more labs and things for students to test in order to learn.
Having a trial version or more training on Splunk would be helpful.
There is a free version, but it is insufficient for training and learning because it is a little bit difficult to work with, especially if you are a beginner. It's difficult to improve when you're just starting out with logs and SOC. As a result, we require a longer free version.
Splunk is not used in my company. During my internship, I am being taught how to use it at school.
I have been using Splunk for one month.
I did not have any issues with the stability of Splunk. It was quite stable.
There was technical assistance available. When you require assistance, they provide it, they will respond.
We integrate Jira with QRadar which is helpful.
The initial setup was simple because there is available support and tutorials.
I completed the installation with the help of some friends, in the IT department.
I'm only using the free version for the time being.
The cost is reasonable.
Splunk's costing is a little more difficult. The pricing method is complicated, and the way that costing is calculated in Splunk is a little more difficult.
When compared to QRadar, QRadar, it's simple to pay.
I did some research for a school project. I needed to compare it to Splunk and a few other tools. As a result, I'm not particularly interested in purchasing them.
I would rate Splunk an eight out of ten.
Our initial use case was for security investigation, with the intention of creating some use cases. We ended up adding operational aspects, monitoring certain operational activities, such as high CPU utilization or any other applicational basis.
This is obviously a cloud solution, but it does have some presence on-premises as well, so it's hybrid.
One of the most valuable features is threat hunting. We can do threat hunting and identify if there is any malicious activity happening within our environment, which is a key feature for us.
Splunk could be improved by reducing the cost. The cost is one of the biggest challenges for us in keeping to our production requirements.
As for additional features, I think they need to refine their AI capability. I know that everyone is talking about artificial intelligence and threat hunting, so I guess one of the key requirements for us is for the solution to automatically provide us some kind of indication and then mitigate any risk. So automation should be a feature.
I have been using Splunk for two years.
This solution is excellent from a performance and stability perspective. There's very minimal maintenance required. Basically the only aspect we need to maintain is the one we have on-prem. So patching up everything and making sure it has the required updates.
There are no issues at all in terms of scalability, since this is a cloud-based solution. There are around 25 to 30 users in my company accessing Splunk.
Splunk's support is good. The process was smooth and they provided sufficient support, so there was no need to escalate anything. Also, they provide training on a regular basis, which is good.
I have never worked with other similar products. I've worked for three companies, all of which use Splunk.
The initial setup was very smooth. I think we got some support from the Splunk team. Since it's a cloud-based solution, it took us probably three or four weeks to actually start working. But deploying agents, configuration, refining, fine tuning, and other ongoing activities went on for about a month.
We implemented through an in-house team with some support from the Splunk team. It was a very smooth process, from our perspective.
This solution is costly. Splunk is obviously a great product, but you should only choose this product if you need all the features provided. Otherwise, if you don't need all the features to meet your requirements, there are probably other products that will be more cost-effective. It's cost versus the functionality requirement.
I also evaluated IBM QRadar and LogRhythm NextGen SIEM.
I work in security architectures, not operations, so I don't actually work with Splunk on a regular basis, but the team that does is working on threat hunting and incident management.
I rate Splunk an eight out of ten.
We use it for application log monitoring.
It is a logging product. Our application generates log files, then we upload them to Splunk. We run their agent on our EC2 instances in AWS, then we view the logs through their product, and it is all stored on their infrastructure.
We have used the alerts for a lot of things. They gave us the ability to kind of make an alert simply. So, we did one for SQL injection. We also had some services which were problematic that would fail, but we figured out what log line that we could look for, so it was easy to make an alert for that.
Its usability is the best part. It is easy for our developers to use if they want to search their logs, etc.
A problem that we had recently had was we licensed it based on how much data you upload to them every day. Something changed in one our applications, and it started generating three to four times as many logs and. So now, we are trying to assemble something with parts of the Splunk API to warn ourselves, then turn it off and throttle it back more. However it would be better if they had something systematically built into the product that if you're getting close to your license, then to shut things down. This sort of thing would help out a lot. It would help them out too, because then they wouldn't be hollering at us for going over our license.
Stability has been great. I don't think we have ever had an outage from it.
We don't do a lot of searching. If there is somewhere with problems, it will probably have to be with a lot of searches, and we don't have that. We don't have many developers searching every day. It is mostly when there is a problem, then we use it for diagnostics. So, we don't put a large search load on it. However, the reliability of it has been great. It hasn't been down for us at any point.
It seems to have worked out great. We haven't had any problems yet.
I haven't used the technical support.
Before Splunk, we used Kibana and Elasticsearch. Sometimes, with them, logs wouldn't even be there. We have received an infinite time reduction there. We couldn't use what we had before, so Splunk being there and working does a lot.
The integration and configuration with the AWS environment was easy. They had the documentation. All we had to do was get their agent running on our EC2 instance, and their documentation was good for that. It worked, which was great.
The product is also integrated with PagerDuty, Slack, and AWS. Those integrations are good and seamless.
It has made life easier for us through use, then by troubleshooting problems. It reduces the cost of the intangibles.
The pricing seems good relative to the other vendors that we have had here. However, they need to find ways to be more flexible with the licensing and be able to deal with situations where we start generating more logs. Maybe having some controls in the Splunk interface to turn it off, so we don't have to change anything in our application.
We have an existing contract with Splunk, so it makes sense to stay with them for now. Our license is for a 100 GB/logs a day.
There are a lot of vendors in the space at the conference this year. Therefore, we probably talked to six or seven different ones, and the market seems to be consolidating. The market's metrics and log monitoring all seem to be rolling up into a single provider. It looks like that is what will be happening in the next few years.
Right now, there are a ton of different smaller providers doing little pieces of this and that. All the big players, like Splunk, New Relic, and Datadog, seem to be rolling them all up into one offering.
Implement something and watch how much data you are sending to it, then have some way to shut it off without redeploying your app in case things get hairy.
We use the cloud version of the product.
Enterprise security is the solution’s most valuable feature.
Its reporting functionality is excellent.
I really like the user interface and how it works.
It’s scalable.
The solution is stable.
You can integrate any other tool or any other solution, including existing solutions, with Splunk. They have a good setup.
The log analysis is something that is good. In general, data analysis is something you can do in Splunk in various ways. You can leverage it as per your requirements or as per your investigations. You can write your own queries and complicated queries, and you can have your own alerts. You can correlate events. It’s very flexible.
It is one of the best tools that I'm using. I don't have any feedback as such right now regarding improvements. I'm not also an expert, so maybe I'm missing something.
Writing queries is a bit complicated sometimes. If they could provide some building queries, that would be great.
It's been a while. For maybe four years, I've used Splunk, however, I'm not an expert on it.
It's a stable solution. We are not going to get rid of it anytime soon. It’s reliable. There are no bugs or glitches and it doesn’t crash or freeze. The performance is good.
The solution scales very well.
I wasn't part of the engineering side, so I never got a chance to contact the support team directly.
We have a SIEM solution, however, now the company is also trying to move to an Excel solution since the automation is better on their side. We aren't going to get rid of it or did not have any other SIEM solution in their mind when they were acquiring it. However, if any XOR solution works perfectly for us, the company might consider moving out of Splunk.
A different organization would have a different setup of Splunk. If you ask me, mostly, it is a simple setup. However, here in my current organization, it is mostly on the cloud, and a lot of things are integrated in a bit of a complex manner. I also understand that this changes from organization to organization in terms of how they will leverage it.
I’ve never looked into ROI and have not been a part of conversations concerning ROI.
I don’t have any idea what the cost of the solution is. I don’t handle the licensing.
A company that wants to leverage Splunk should understand its environment first - including the organization, the network infrastructure, and the overall infrastructure. Then, based on requirements, they should go ahead with any SIEM solution. Splunk is kind of an expensive tool to have. Therefore, the company should be clear about what requirements they have, what they need, and whether they want to use Splunk. It is very crucial to understand your requirements and your network or your environment first before going ahead.
I’d rate the solution eight out of ten.
Overall, it's a good tool. It's a very intelligent tool. It definitely depends on how you are going to use it. However, I love the product. I love Splunk. I want to learn more about it as much as I can.
We are a solution provider and Splunk is something that we provide as a service to our customers.
The most valuable feature is the reporting and the information that is provided by the tool.
It is very easy to implement a PoC using Splunk, which will show the value of the reporting and data that it provides.
The integration is seamless with many devices and operating systems.
It is flexible enough that you can choose what kind of deployment model you want.
They have a large solution toolkit that supports IoT, wherein businesses can get a lot of help with the centralized management functionality. There are also tools to assist from the security and SIEM perspective, and there is a centralized dashboard.
Being a SIEM solution with a centralized dashboard, we would like to have more options to customize it. It should be easy to customize dashboards.
When we are monitoring something, we would like to have a more granular outlook. Splunk has a good dashboard that is easier to use than some competing products, but better customizability would be a great help for the users.
We have been working with Splunk for approximately three years.
This product is very stable.
Splunk is a very scalable solution. Being a Japanese product, they will ensure that all of the features work in any environment. It is very heterogeneous. It can integrate with Windows, Linux, AIX, HP-UX, and Solaris. It also supports IoT devices, mobile phones, and more.
We have more than 150,000 people using our services.
The Splunk team has good, proactive support. Also in terms of assisting with the installation, they are quite good.
Splunk is similar to IBM QRadar, which we also have experience with. However, Splunk has advanced SIEM features included with it, so we often use it to satisfy this requirement. Whenever an organization is looking to implement SIEM, they have the flexibility to choose Splunk, QRadar, or the ArcSight Logger solution.
One of the major differences that I see between Splunk and QRadar is that Splunk gives the users fewer devices, so they can do things quicker.
The installation for Splunk is easier than competing products QRadar and ArcSight.
We have Splunk deployed on the cloud so that we can provide the service, but some of our customers have it installed on-premises.
All the user has to do is download the Splunk server agent, install it on the laptop or endpoint, integrate 50 or 100 devices, then see what kind of reporting is available.
We have an in-house team for deployment in maintenance. Splunk is a tool that does not require much staff to maintain. The users can start with a PoC, simply learn it, and deploy it for themselves. They don't require subject experts to be hired for the installation and configuration.
Price-wise, if you compare QRadar to Splunk for SIEM functionality then they are in the same range but when you integrate SOAR with these solutions, Splunk takes the lead and is more competitive.
This is a product that I recommend for anybody who wants and advanced SIEM solutions. Of the three that I have used including QRadar and ArcSight, Splunk is the one that I prefer.
I would rate this solution a nine out of ten.
The ease of log connection has been great.
Its compatibility with other SIEMS is very useful.
They have many basic use cases that we like.
The cloud version of the solution is especially scalable.
The product has been quite stable so far.
The initial setup is very easy.
Technical support is lacking post-sale.
The modification of firmware could be improved.
We find that the maintenance process could be a lot better.
The solution is more expensive than other options on the market.
We haven't been using the solution for too long at this point. It's been about four months or so.
The stability has been good. It offers good performance and doesn't seem to be buggy. There aren't glitches. It doesn't crash or freeze. It's reliable.
The solution is scalable. This is especially true for the cloud deployment model. There really isn't anything holding you back if you use that version.
We have around 100 people on the solution currently. 60 to 70 of those are technical users.
We do plan to keep using Splunk.
Technical support services are lacking, especially after you buy the product. They aren't as helpful or responsive as we need them to be. However, when we do reach them, they are good and they help.
I have used McAfee Nitro in the past and IBM QRadar as well.
The initial setup is not complex. It's very straightforward. In fact, it's far easier to install than other log tools on the market. A company shouldn't have any issues with the process.
That said, I did not work on the installation myself. Other people at the company handled that aspect of the process.
The maintenance process could be better. It's a bit difficult once the deployment is done. We need about five people for maintenance tasks.
When you compare the services and features, the pricing is reasonable. That said, if you compare Splunk to other options on the market, it is more expensive.
As we recently purchased the solution, we are using the latest version right now.
I would recommend the solution to other users.
I would rate the solution at an eight out of ten. If the solution offered a better price and better support services, I would likely rate it higher. However, for the most part, we have been satisfied with the product and its capabilities.


thank you for a good review.